With so many emails in circulation these days, it can be difficult to know what’s real and what’s fake.
Scammers send around 3.4 billion spam emails every day, with stolen credentials being the most common form of data breach. Many of these breaches are due to phishing and email spoofing.
In this article, we explain what email spoofing and phishing is and share ways to help you protect yourself from being scammed.
Phishing Explained
Phishing is a form of online scam where cybercriminals pose as a trusted person, brand, or business to obtain sensitive or personal information.
Phishing scammers usually target victims through communication channels, including email, SMS, WhatsApp, and social media.
In addition to stealing personal information, many phishing scammers also aim to:
- Obtain financial details including online payment logins, bank account credentials, and credit card numbers.
- Capture login credentials for apps, corporate accounts, email, and social media profiles for identity theft purposes.
- Trick people into installing malware to gain control of their laptops or devices.
How Does Phishing Work?
Phishing is a scam that exploits trust. It’s a form of social engineering where the scammer gathers basic information about the person or organisation they’re looking to impersonate.
Scammers then choose a communication channel to target victims and create messages that bait victims into clicking on a link, downloading a document, or sharing personal information.
Most phishing messages give recipients a convincing reason to engage, often by creating a sense of urgency or triggering an emotional response.
The scammer uses their victim’s information or credentials to commit fraud, steal their money, or even sell their data.
Email Spoofing Explained
Email address spoofing is a malicious act that involves forging a person’s email address. The aim is to trick recipients into thinking the email comes from a trusted source.
In email spoofing scams, the sender forges the email header so that it appears legitimate. Scammers often use email addresses that look very similar to those of genuine companies, with small differences that are easy to overlook. This can make the email seem authentic, especially if the sender’s name is familiar. It’s important to always check the full email address carefully, not just the display name, to spot any subtle variations that could indicate a scam.
Email spoofing is usually used to encourage people to click on malware attachments or share sensitive information.
This type of malicious online scam has been a pressing issue since the 1970s, mainly due to the way email protocols work, which allows scammers to get past email filters.
Email spoofing became more prevalent in the 1990s, before growing into a worldwide cybersecurity threat in the 2000s.
Security protocols were developed in 2014 to tackle email address spoofing and phishing, which means many of these fraudulent messages are now blocked or sent straight to the spam folder.
How Does Email Spoofing Work?
Outgoing emails are retrieved and routed through the Simple Mail Transfer Protocol (SMTP), which is essentially a digital postal service.
An SMTP defines how an email client (such as Outlook or Gmail) and server communicate with one another, and how these messages appear when they arrive at their destination. The problem is that these SMTP protocols have vulnerabilities.
Scammers exploit these vulnerabilities by using scripts to define which email address their messages appear to be from. Email headers can reveal the true route and sender of an email, but many users don’t check them as they already believe it to be legitimate by looking at the ‘From:’ field.
As SMTP protocols don’t validate whether an email is legitimate or forged, many phishing and spoofing scammers also use the ‘Reply To’ field, which can differ from the sender address.
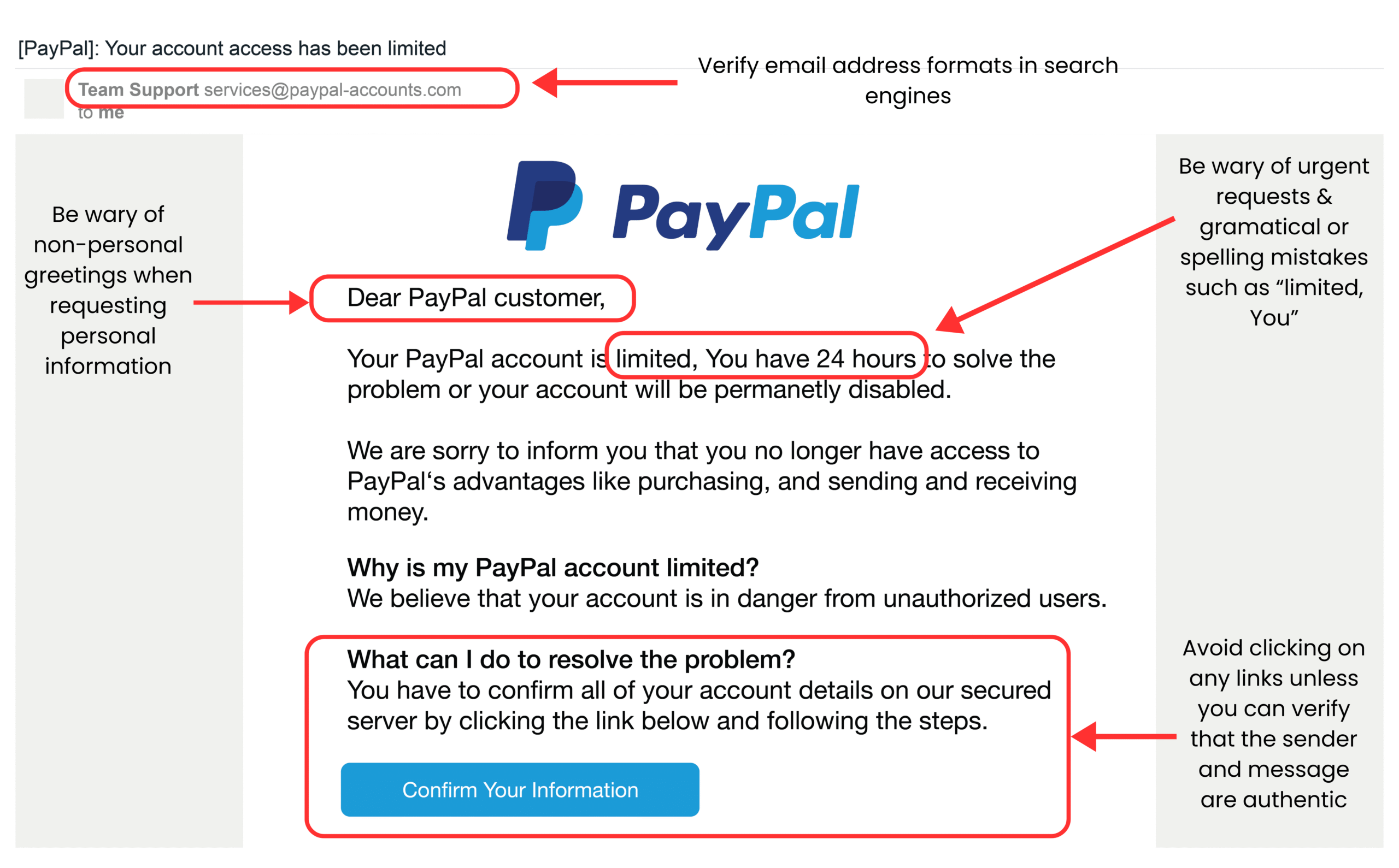
How To Check If An Email Is Fake
Knowing how to check if an email is fake is an essential part of phishing or email spoof prevention.
Here are the best ways to identify whether an email is legitimate:
- Examine the email header if you have any doubts about its origins.
- Check if the email address matches the display name.
- Look out for grammatical errors, spelling errors, and an urgent tone within the message as it’s usually a telltale sign of phishing or email spoofing.
- Be aware of personal information requests that seem jarring or unusual.
- Keep an eye out for strange email addresses or domains—@hmrc.tax-help.com, for example, is a common phishing domain style.
- Be wary of any generic or impersonal greetings. If a sender doesn’t use your name, it could be a scam.
- Don’t click on or engage with any suspicious message attachments or links that display strange URLs when you hover over them.
- Copy and paste the email’s content into a search engine to check if it’s been reported as spam.
- Think twice about any unusual requests such as ‘provide your login details’, ‘send a payment’, or ‘please click this link’.
- Avoid clicking any links or sharing any information unless you’re 100% certain it is safe to do so.
- Use an email spoofing checker to see if the header or domain is legitimate.
Common Email Scams: Real-World Examples
With a significant rise in AI tools and global events being used as prime clickbait, regularly evaluating scam tactics is more important than ever.
Being aware of these common email scams will improve your awareness, help you stay safe online, and reduce your risk of falling victim to cybercrime.
HMRC Impersonation Email Scams
HMRC impersonation scams are becoming an increasingly common way of obtaining bank details or sensitive login information.
Scammers typically trick victims by claiming they’re owed a tax refund or face a fine. Remember, HMRC will never ask for sensitive details via email or messaging apps, so if you receive a suspicious email from this source, delete it.
Gmail Phishing Scams
Many scammers exploit Gmail or Google Alerts to warn victims of suspicious login activity or maxed-out email storage.
Be aware that these emails or messages will include a fake link to “secure your account” which can lead to credential theft.
Facebook Phishing Scams
Emails or messages informing you that your Facebook account has been reported or disabled are another common form of phishing scam.
These messages typically urge you to “verify your identity” via a malicious link. This scam tactic can also apply to other social media channels, including LinkedIn and Instagram.
Crypto Phishing Scams
These phishing scams usually involve scammers impersonating crypto exchanges or wallets with urgent security alerts.
Most crypto phishing messages ask for seed phrases or wallet credentials. If you receive a message asking for any of your cryptocurrency information, disregard it and avoid engaging with any links or requests.
Email Scam Prevention Tips
By prioritising security and putting the right processes in place, you can reduce the threat of email spoofing.
You should be cautious of every message you receive and verify email senders to check they’re legitimate. You can also use email security platforms to block or flag suspicious content.
On a business level, you can follow these email spoofing prevention practices to reduce your risk:
- Put email authentication protocols in place: Sender Policy Framework (SPF), Domain-based Message Authentication, Reporting, and Conformance (DMARC) protocols, DomainKeys Identified Mail (DKIM) can work together to authenticate emails while preventing spoofing.
- Provide email spoofing and phishing awareness training: Educating your staff to spot, avoid, and report potential phishing or spoofing emails will significantly reduce your risk of being attacked.
- Use a secure provider: Choosing an email provider that is known for its robust security features can protect your business against email spoofing or phishing.
Concerned you’ve shared information with a suspicious sender?
Email spoofing and phishing are rife today. But by knowing what to look out for and putting the right protocols in place, you can significantly reduce the risk of being caught out by potential scammers.
For further guidance on spotting and avoiding potential online scams, visit our resource centre.

